Proxy Pattern
(from Design
Patterns)
Synopsis
Provide a surrogate or placeholder for another object which cannot be
accessed by normal means.
Context
You want a normally inaccessible or unavailable object to appear like
an ordinary object. For example, the object might be:
-
in a different process
-
in a disk archive
-
compressed
-
not computed yet
Forces
-
Turning an object into a Proxy, or vice versa, should be transparent.
Solution
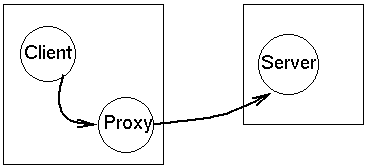
Make a Proxy object with the same interface as the subject and which holds
a reference to the subject. This is usually not a conventional reference,
but may be a
-
host/port/object triple
-
file name and offset
-
piece of code for producing the subject
The Proxy may forward requests to the subject or simply replace itself by
the subject, depending on the Proxy's purpose.
This solution looks like a Decorator and may
be implemented by identical means but it is not accompanied by the same
policy. A Decorator adds capabilities to an object; a Proxy is a bridge to
an inaccessible object. Since a Proxy is not an addition to the object it
stands for, there is no need for delegation as in the Decorator pattern.
(However, there is still a use for the hot swap technique.)
Consequences
-
The normal inaccessibility of the subject is transparent.
-
Since the Proxy has the same interface as its subject, they may be freely
interchanged.
-
Subjects generally do not access their own Proxies. First, the
Proxy is usually just as inaccessible to the subject as the subject is to
the Proxy. Second, the Proxy is not a real object but just a "mirror
image" of the subject.
Implementation
-
A Proxy can cache stable information about the subject to postpone
accessing it. Caching can also be done with a separate cache Decorator. Caching should be done with caution
since the subject generally does not access the Proxy and so cannot
invalidate the cache.
-
The hot swap was introduced as a technique for transparently
introducing and removing a Decorator. It is
also useful for transparently introducing and removing a Proxy.
See Design
Patterns for sample code.
Known Uses
-
Proxies are commonly used to make objects appear local in distributed
systems. For example, the client stub which initiates an RPC is a Proxy
for the server function. NEXTSTEP extends this to objects via the NXProxy
class. CORBA uses Proxies so that database objects can be treated as
native language objects.
-
Lazy evaluation in Scheme is based on Proxies which encode a pending
computation. Once the value is needed, the computation is executed and the
Proxy is replaced by the output. This technique is used to implement streams.
-
Copy-on-write is a special kind of lazy evaluation used in Matlab.
Where a matrix would normally be copied, only a Proxy is created.
Reads to the Proxy get forwarded to the original matrix. Writes
force the Proxy to replace itself with a real copy. This technique
automatically cuts down on spurious copies and lets Matlab code be simpler
without hampering performance.
Thomas Minka
Last modified: Mon Jan 20 17:14:18 EST 1997
